This article is the second installment of our ongoing security series.
Having all your important tasks and stats held in a service provider’s cloud storage is now normal. As we covered in our first data security post, this means good data security hygiene is a collective effort, led by managers that organize team members’ tool access mindfully. Software as a Service, or SaaS, has reframed software as a licensed subscription that is accessible online rather than relying on local storage of the tools and user data. Organized by user permissions, access to information and its controls can be precisely managed.
Ideally, the responsibility of orchestrating this at a high level falls to a company’s IT manager – but if those tasks fall to general operational managers, like they might at a smaller farm, it’s even more important to intentionally take stock of who has access to what at regular intervals.
Implementing the principle of least privilege through permissions
No matter where a company is at with its security and organizational practices, the base approach relates to the principle of least privilege. This concept originates from a computer security design paper produced by researchers Jerry Saltzer and Mike Schroeder in the early 1970s. It anchors a reasonable standard of security throughout the team with a simple premise: permit the least level of data access possible across all members, while still allowing operations to run. Provide employees the view and control they need to accomplish their responsibilities in a safe manner by restricting access to anything extraneous. That way if there is a security breach, there is a fighting hope of detecting and managing the exposure. Odds are, the account that was compromised doesn’t hold the keys to every metaphorical locked door.
Even though the principle of least privilege has existed for several decades, the execution and adherence to this remains challenging for most organizations. Among the challenges can be team concerns around trust and transparency, particularly if a permissions audit rolls back access to some without adequate education around why things have changed. It’s not personal, but it might feel like it is.
The best way to combat this? Let all stakeholders in on the process of defining privilege access levels, whether it’s for a new system from scratch because you’re making a big switch from analogue to digital record keeping, or the implementation of a fresh audit process for long-used tools. Then everyone can see the ‘why’ of the process, and weigh in on what access is valuable to their own work. Less hiccups, more clarity – a more secure team emotionally and digitally!
Where possible, allocating access to roles rather than to specific individuals is far more manageable to maintain least privilege access from an operational perspective. This is especially helpful when staff move within the organization frequently. In a farm production environment, the seasonality of field labor can mean roles are filled by different individuals at a higher frequency than other industries.
How Croptracker utilizes permissions
Within Croptracker’s farm management platform, accounts have users with customizable permissions through top-level access controls, and definable role statuses. The function of permissions here goes beyond security breach concerns, as partitioning view and access can also ensure detailed information is accurate. With fewer cooks in the kitchen, there’s less potential for confusion.
Role-oriented permissions are more apparent in some areas of Croptracker than others, but the capacity to customize who can see what is available throughout the platform. Designed for tracking spray inventory and application events, the Spray module is a great example of how role-based access uses least privilege to improve production accuracy. The following is an example of how permissions function within the Spray module, accompanied by a cropped screenshot example of Croptracker’s desktop app.
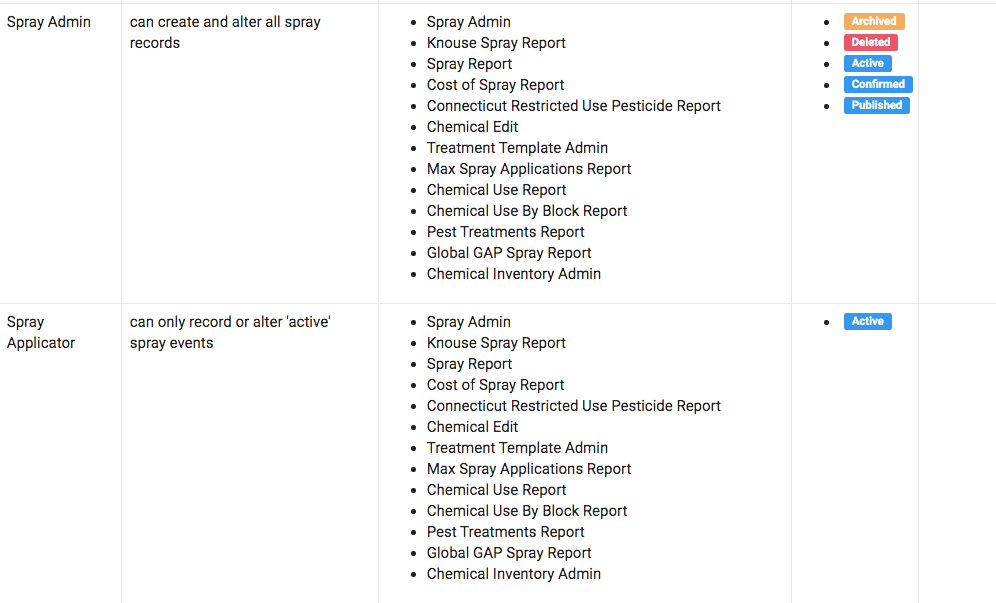
This example features the permissions view for two roles within the Spray module: the Spray Admin, who can create, access and edit all spray events; and the Spray Applicator, who can only record or alter ‘active’ spray events. This configuration ensures that the Spray Applicator only sees what currently requires attention in the field ensuring work orders are completed properly and spray details are kept accurate for auditing.
In the case of accounts with more than one location, additional limits to user access are available. Users can be limited to just seeing information for the farms they are working on, while operations managers can see information from all farm locations.
Farm management tools à la carte
When software is modular, there’s no need to pay for tools that won’t be used. Croptracker subscriptions are priced by module and by how many user seats are required for your team. Depending on what’s needed, there may be more users initialized for some tools than others, meaning tracking and data processing is neat and tidy, as well as affordable. Have a question about how to best organize users, roles, and permissions in Croptracker? Get modules, locations, and users orchestrated the right way from day one by booking an appointment with a member of our support team.


