This article is the first part of our ongoing security series.
It’s not a new piece of advice: where there’s a login, there’s risk of security breach – following best password practices will provide protection and reassurance. The threat of having data compromised is widely understood, but research suggests that commitment to digital security remains lax for most individuals from its American sample. So maybe... the Dos and Don’ts are a little foggy.
A good, strong password

What makes a password strong? It’s uniquely associated with each login you’ve got, it’s long, and it’s been tossed out and replaced at a regular interval. One or two short, catch-all entries for everything you use might have been okay back when it wasn’t commonplace to upload your whole life and work to SaaS products. Things have changed! Organizations like Electronic Frontier Foundation advocate for passwords made up of a minimum of six random words, best chosen through an approach called the Diceware technique. Created by Arnold G. Reinhold, the Diceware technique involves rolling six dice to determine a string of six numbers. Each string correlates with a wordlist entry – repeated rollings will lead you to a truly randomly generated password able to thwart most cyberattacks.
Storing everything in a secure place
Long and nonsensical passwords are not suitable for memorization, which is why password managers have grown to be a common and important tool throughout one’s day. Opting in to the password management functionality of your preferred browser is better than using nothing – it’s a free option that doesn’t require much setup and you can add logins as you go. But if you’re switching between devices and browsers on a regular basis, looking for something beyond basic features, or have shared logins with a team, there’s considerable value in choosing a third-party password manager.

Third-party password management services offer cross-platform and cross-browser connectivity. The features vary between products, but broadly fall under the same buckets of secure storage, organization, and sharing. Check the strength of existing logins and generate new ones with the suitable length and types of characters, and some tools will even flag if your password correlates to any recent data leaks. The top password management products currently include 1Password, LastPass, Bitwarden, and Dashlane.
Check for data breaches
In spite of all best efforts to protect sensitive online data, it’s still possible to be impacted by data breach attacks aimed at the companies you create accounts with. If you’ve already assigned unique passwords to each of your logins, then the individual impact will be minimized. Major cyberattack events are newsworthy, so these are more likely to provoke changing your passwords. But when it’s a smaller company that’s compromised, affected users may miss that it occurred – particularly if it’s an old or inactive account that’s no longer regularly monitored.
One helpful tool for staying up to date on data breach risks is Have I been Pwned, a site that documents data breaches and whose information has been caught in the midst of them. A free resource, Have I Been Pwned references the gamer and hacker Leetspeak term for being controlled or compromised. Enter an email or password into its search bar, and the site will check the logs of all aggregated breach data to see if the query appears as a result, and which breaches it is associated with. Some information on each relevant breach event is included for context on when and how a company’s data was exposed. Emails and passwords are stored separately without personally identifiable data, and all passwords are SHA-1 hashed, further obscuring them. If your login credentials end up on one of these lists, ensure anything corresponding to the affected email or password has been updated since the time of the breach’s occurrence.
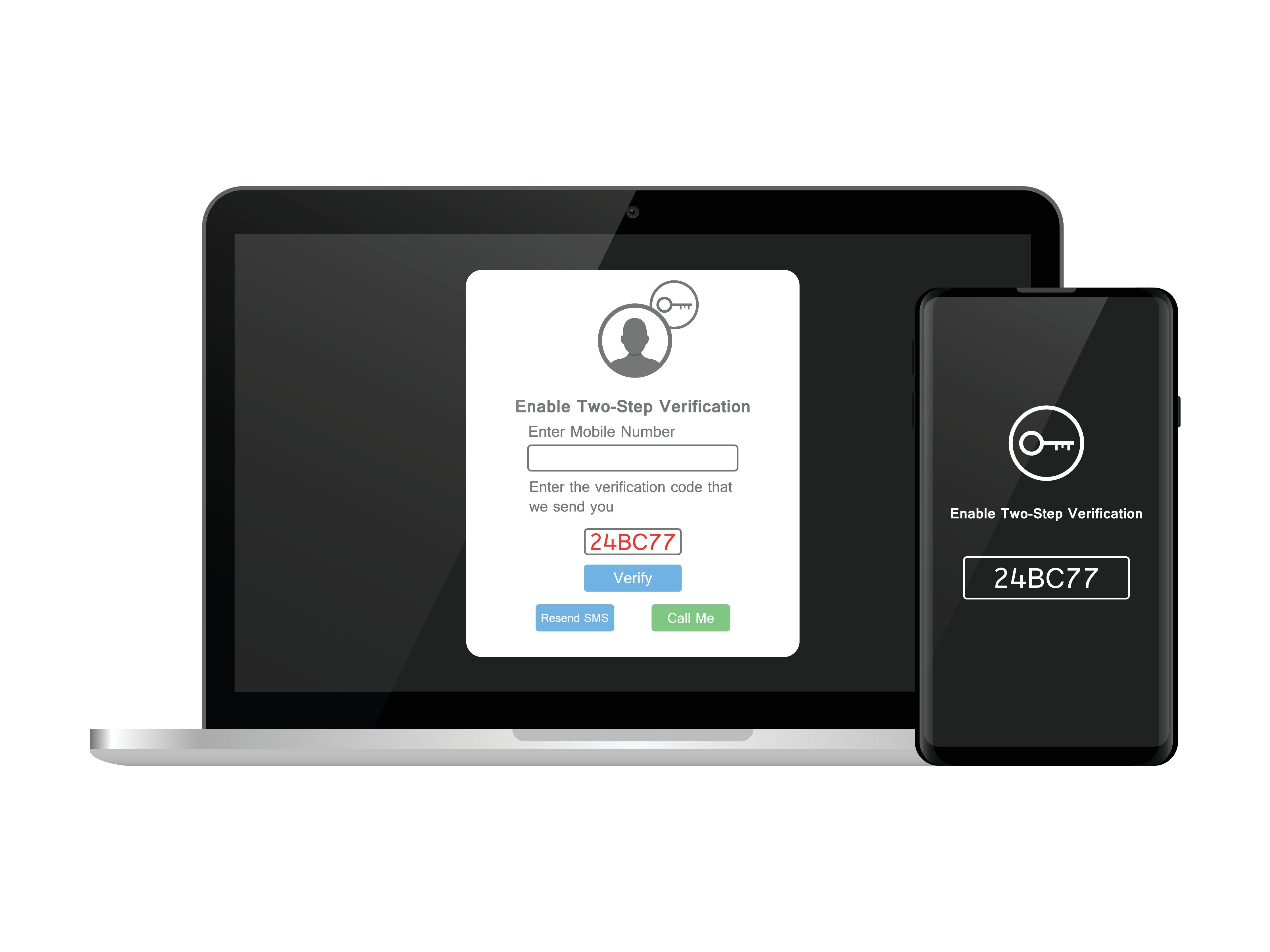
Extra user-side insulation from data breaches is available from some larger scale services and networks offering two-factor authentication (2FA) as part of login procedures. Add this step to more accounts through separate services like Twilio’s Authy. Two-factor authentication creates an additional step to verifying an account access by requiring a time-sensitive code to be entered after the standard login attempt. This code is typically sent by the service provider to a device, like a text message to a phone. Using 2FA can be a bit tedious to get used to, but it is an easy way to add a layer of protection to your data security.
Staying up to date on the latest data security hygiene recommendations is just one way to hand off some of the mental load involved with digital information management. Croptracker is another resource for externalizing your daily operations and ensuring your important recordkeeping is all in one place.
Interested in learning more about Croptracker? Learn more about our Farm Management Software, or book a demonstration to schedule a meeting with our product experts. For support please e-mail us at support@croptracker.com or start a Live Chat with us by clicking the green speech bubble in the bottom right-hand corner. We're always happy to help you make the most of Croptracker to make your farm more efficient, safer, and more profitable!


